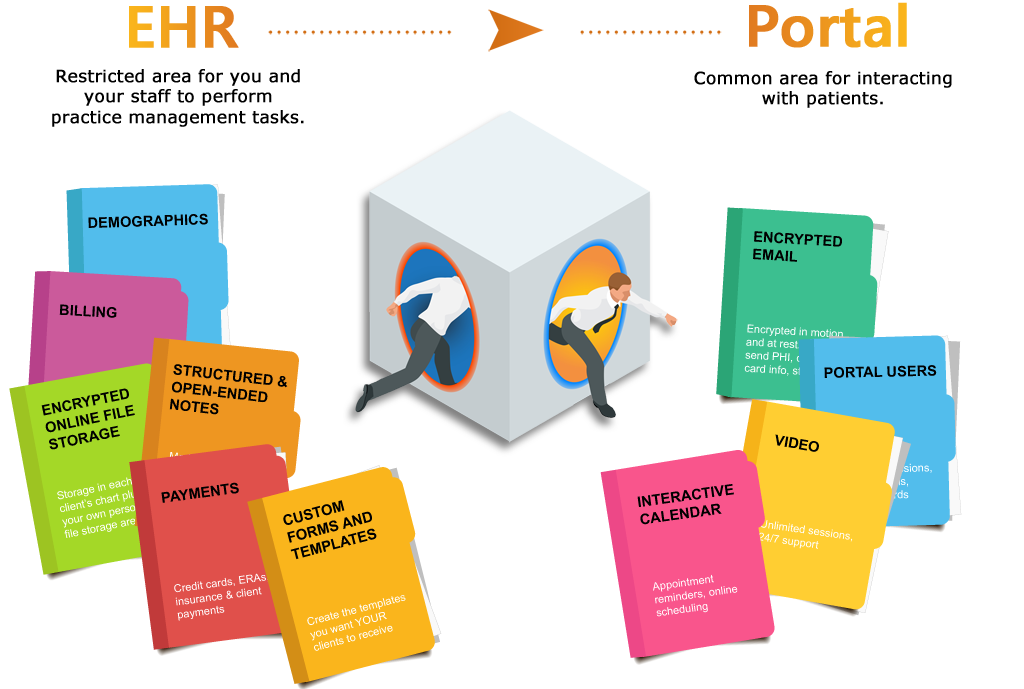
Doing Telehealth? You Need a Portal.
Think you're not doing telehealth? Think again. Although there's no one-size-fits-all definition that cuts across state and/or discipline lines, most agree that telehealth basically involves any electronic method you use to communicate with or about your clients. This can include common things like phones, email and electronic file storage, in addition to video sessions, which is what we typically think of with the term telehealth.