I often find myself telling mental health providers that two of the best things they can do to be in compliance with HIPAA while also saving both time and money is to use integrated products that are 100% end-to-end encrypted. I’ve said that so often that I don’t really think about it. It’s my go-to response. Recently I had someone ask how to tell if a product is “100% end-to-end encrypted.” That gave me pause. It was a VERY astute question that no one had asked me before, nor had it occurred to me that it needed explaining. But it does. It so very much does. Here goes:
What is End-to-End Encryption?
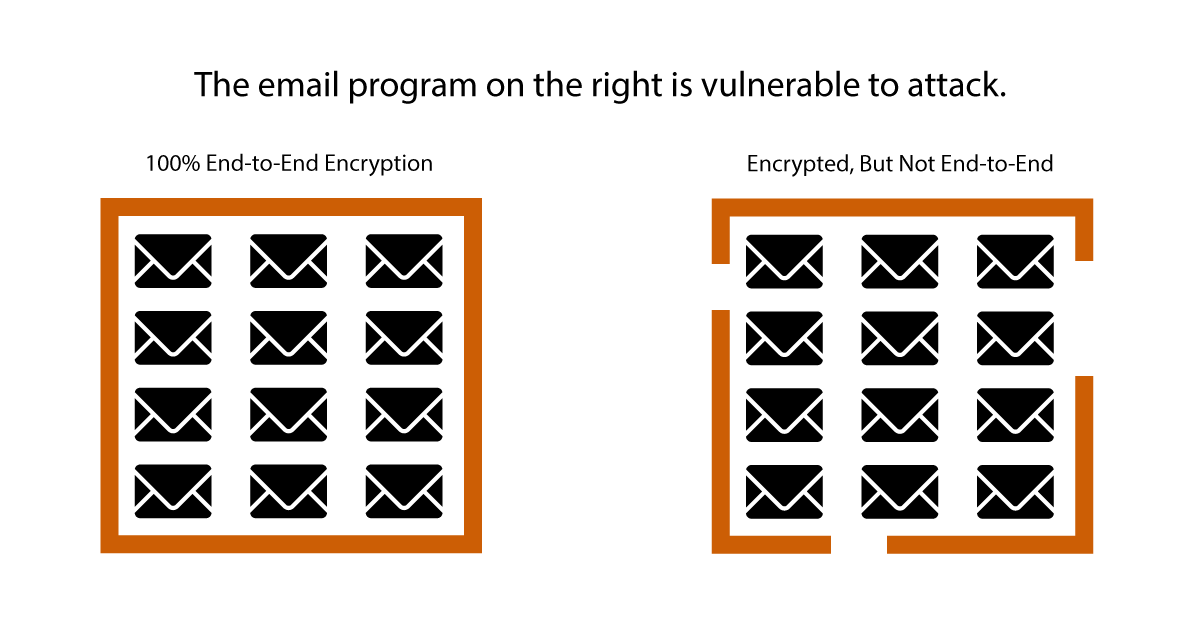
The term “end-to-end encryption” means that data is encrypted from the moment it leaves your device all the way through to when it lands on the recipient’s device. It can not be decrypted or read anywhere along the route, even by employees of the software company. It’s encrypted in their database and they don’t have a way to decrypt it. Only the intended recipient does. In a sense, end-to-end encryption creates an impenetrable universe. Everything within that universe is secure. There are no holes.
In contrast, products that are not encrypted or are only partially encrypted DO have holes. Parts of those products may be encrypted, but they do not form an impenetrable universe. They can be accessed and files read at various points along the way. If a hacker chose to, they could post the content on the internet or do anything else they wanted to with the information.
This issue comes up most often with email and texting, so we’ll discuss it within that context. Graphically, the two types of encrypted products can be depicted like this:
Why is 100% End-to-End Encryption Important?
HIPAA specifies that all healthcare apps must be encrypted. However, HIPAA does NOT indicate what kind of encryption is required. Because of this, software companies often correctly claim their product is HIPAA compliant even though it is only partially encrypted.* Because the Security Rule requires us to keep all PHI secure, if we choose to use one of these partially encrypted products and there’s a breach, HIPAA can and does impose fines and possibly other sanctions. We see this most frequently with email, but the rule is the same with all types of PHI: we’re responsible for keeping it secure. The authors of HIPAA realize that mistakes and oversights happen. They are not unforgiving. However, if a provider is using software that is either totally or partially encrypted, the way HIPAA views it is that the provider is willfully disregarding the law. For the provider to proclaim, “Oh! But I didn’t know that!” just compounds the issue. We are required to understand the laws pertaining to our profession. Claiming we didn’t know the product we were using was vulnerable could result in additional fines for not knowing. Which leads us directly into the question I was recently asked:
How Do You Tell if a Product is 100% End-to-End Encrypted?
Short answer is that it is not easy or obvious. Encryption happens behind the scenes. An end-to-end encrypted product looks exactly like a partially encrypted one to the end-user. The difference is under the hood, which isn’t easily discoverable, even by those in the know. The only thing we really have going for us is that companies are required to be transparent about what type of encryption they use. If their product is not 100% end-to-end encrypted, they must say so. However, this is often buried in the fine print because they’re trying to get sales. Admitting that their products are not 100% end-to-end encrypted is a turnoff to potential subscribers. For this reason, they come up with really compelling terms on the main pages of their sites. However, no other description really works here. Terms like “state-of-the-art,” “HIPAA-Compliant,” “endorsed by so-and-so,” and so forth don’t cut it. We need to know that our data is encrypted all the way through. We need to know that the company’s employees can’t access the content of our files. If you can’t find the term 100%-end-to-end encrypted somewhere on their website, write and ask them. The answer to this question should only be Yes or No. If they go into some long-winded explanation of how great their encryption is, you can probably assume that the answer is No.
I also wouldn’t put much stock in software companies that have various types of HIPAA Certifications posted on their websites. I’ve known of at least two software products that carried those certifications that had features that I knew were hackable. Although I do know a lot about this stuff, I’m not a trained security expert. If someone at my level of understanding was able to see vulnerabilities in those two products, it doesn’t give me much faith in the companies that were proclaiming them safe and HIPAA compliant.
How Integrated Products Fit into the Mix
In addition to the encryption piece, it’s also important to use products that are integrated. Integrated products are called by several different names. The most common ones are Electronic Health Record (EHR), Electronic Medical Record (EMR) and Practice Management System. Originally, each of these terms was defined differently. However, as time passed, lines of distinction – blurry to begin with – have become non-existent. Because of that, what you call it doesn’t matter much. But what it does is extremely important to understand. In addition to being more secure, a good integrated product will save you a lot of time and, in most cases, money.
You should expect two things from an integrated product:
- It should be encrypted. If it’s not one of the 100% kind, find a different product.
- It should be “integrated.” This means that each tool or feature the product has is integrated with all other features. So, for example, if your patient changes their name, you should only have to enter that change one time. This is very different from entering the change once on your demographics sheet, again in your email program, again for texting, billing, appointment reminders, video sessions, etc.
Some products add new features helter-skelter without actually integrating them. In another post, I’ve referred to those as three-room-house types of products, equating them with home remodeling that adds new rooms as required but doesn’t take the extra time to integrate them seamlessly into the whole. Those types of EHRs will cause you more headaches than they’re worth and may also have additional security risks than an integrated program will have.
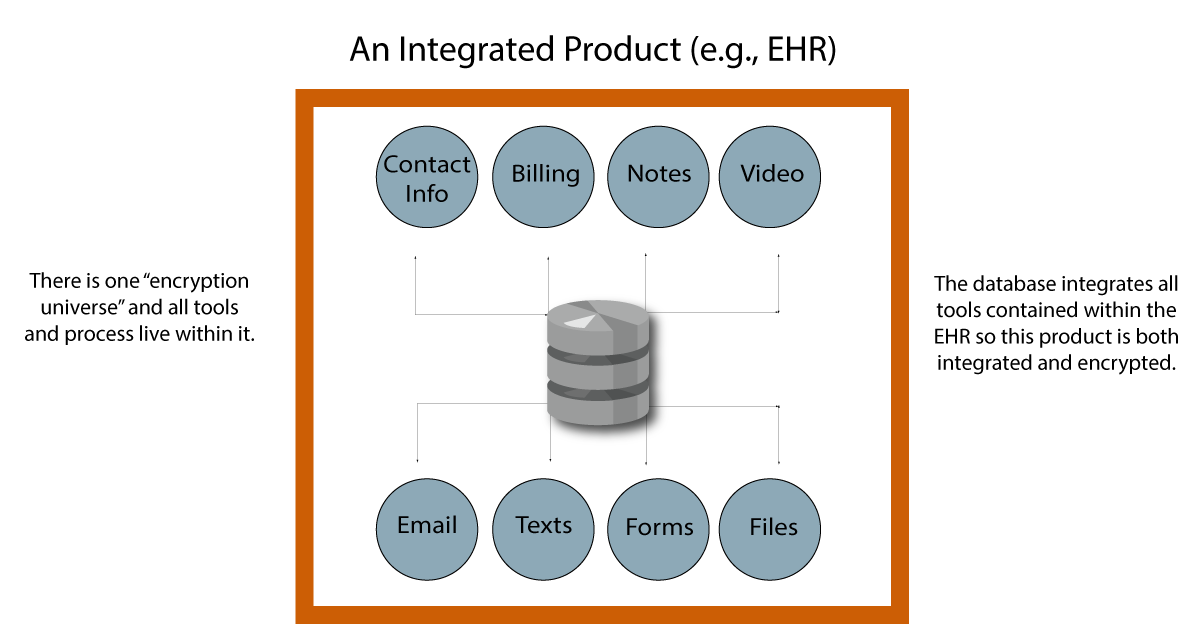
The diagram below represents a well-integrated EHR. Everything within the orange box is secure. Also, the medical record of each patient is stored in one place. It’s all within the orange box. The database in the center integrates all features so that a change in one tool will be reflected in all:
The user in the next diagram has the same set of tools as the previous provider. However, this individual purchased them as separate products. They do not have an integrated package. Notice that a couple of the tools (Billing and Video) are encrypted within themselves, as represented by the orange borders. But the encryption of these products does not extend to any of the others. There is no “encryption universe” that keeps all tools secure.
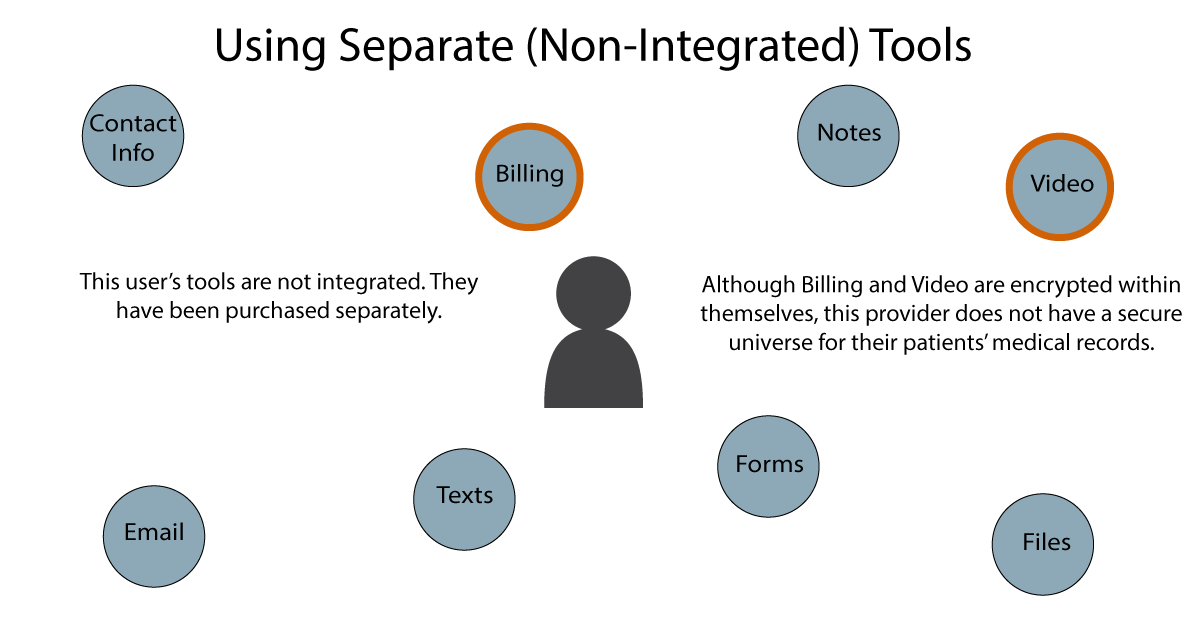
In summary, end-to-end encryption is a must-have, in my opinion. Whether you also want an integrated product is up to you. However, we are required to keep medical records on each of our patients and, at times, must produce them. When a patient’s medical record is scattered among several different places – perhaps some digital, some paper, it’s up to you to pull it all together into one thing. Although it is theoretically possible to find ways to transmit data from one product to another and keep everything secure, it requires a fair amount of extra work. Also, it’s often quite difficult to figure out how to do it without introducing holes in the encryption. Finally, as part of our Security Policy, we’re required to document exactly how we ARE performing those transfers. With an EHR, the security work is done for you. The only thing you have to write up for your Security Policy is that you’re using XYZ EHR.
________________________
*Legally, only Covered Entities can be HIPAA-Compliant. Because of that, software can’t actually be HIPAA-Compliant. Common usage of “HIPAA Compliant software” refers to software that, if used correctly, enables the CE to be HIPAA-Compliant.